- About
- Solutions
- Essentials
- Utilities
- Publications
- Product Delivery
- Support

Keith B. Evans
Product Management
Malware and Ransomware have become massive and potentially existential threats. A comprehensive defense requires multiple layers of protection, including strong Data Resilience.
This comprehensive defense is evolving. It is being developed based on best practices as defined in NIST Cybersecurity Framework.
We recently released a web page describing the Digital Resilience landscape and how HPE Shadowbase software provides new approaches to thwart these attacks.
HPE Shadowbase software provides unique Data Resilience capabilities for NonStop users since it integrates with the NonStop transaction logging facility, TMF, to assist with data recovery should an attack occur. Using TMF provides ACID transaction protection, guarantees all database changes are logged, and enables HPE Shadowbase to use the Audit Trail change data for synchronizing a target environment and for data recovery.
Additionally, HPE Shadowbase detects and prevents Man-in-the-Middle attacks between its processes, which could disrupt critical backup processes and corrupt recovery data.
HPE Shadowbase facilitates adherence to the 3-2-1-1 backup strategy so that companies can replicate data into immutable storage and quickly recover on an air-gapped, isolated (and hence fully protected) system.
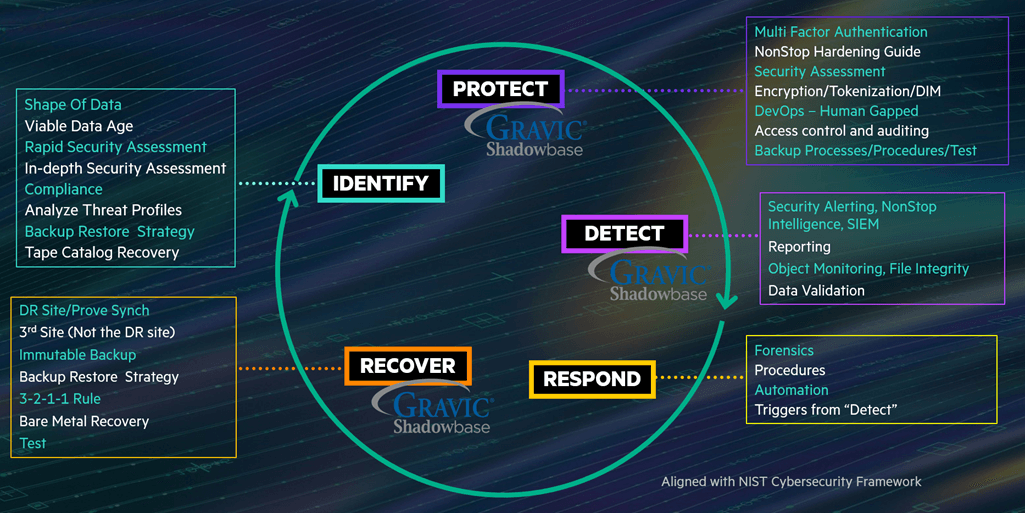
The HPE Digital Resiliency Framework based on the NIST Cybersecurity Standard
Gravic published the article, Ransomware Protection and Data Recovery, in the September/October issue of The Connection, based on our Demo at the HPE BOOTH during the Connect NonStop Technical Boot Camp (TBC).

With this increase in attacks, reliability and data integrity are now at the forefront of business concerns and a primary challenge for businesses to solve. In this article, we review Ransomware detection and recovery architectures, including immutable backups and air-gapped systems. We also review the HPE Shadowbase Ransomware Demo architecture that assists businesses with resolving the expanding set of unique challenges that Ransomware poses.
In case you missed our presentation or the HPE BOOTH DEMO at the TBC, this article will explain how to recover critical data in a timely fashion on a Ransomware Recovery Solution (RRS) system.
Contact Us to discuss your specific requirements.
Specifications are subject to change without notice. Trademarks mentioned are the property of their respective owners.
Please reference our Newsletter Disclaimer.