- About
- Solutions
- Essentials
- Utilities
- Publications
- Product Delivery
- Support
Enterprises around the globe are racing to protect themselves because Malware and Ransomware have become massive and potentially existential threats.
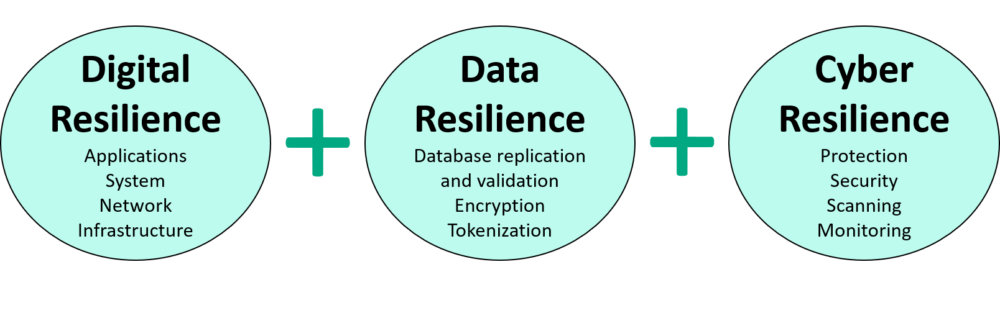
A comprehensive defense requires multiple layers of protection, including strong Data Resilience.
Gravic has provided Digital Resilience solutions for 40+ years: use HPE Shadowbase software to replicate data into immutable storage* and quickly recover applications on an air-gapped*, isolated*, and hence fully protected system.
Malware and Ransomware Recovery architectures require an innovative approach with distinct personnel, processes, procedures, hardware, software, and infrastructure from existing Disaster Recovery (DR) and Business Continuity (BC) architectures.
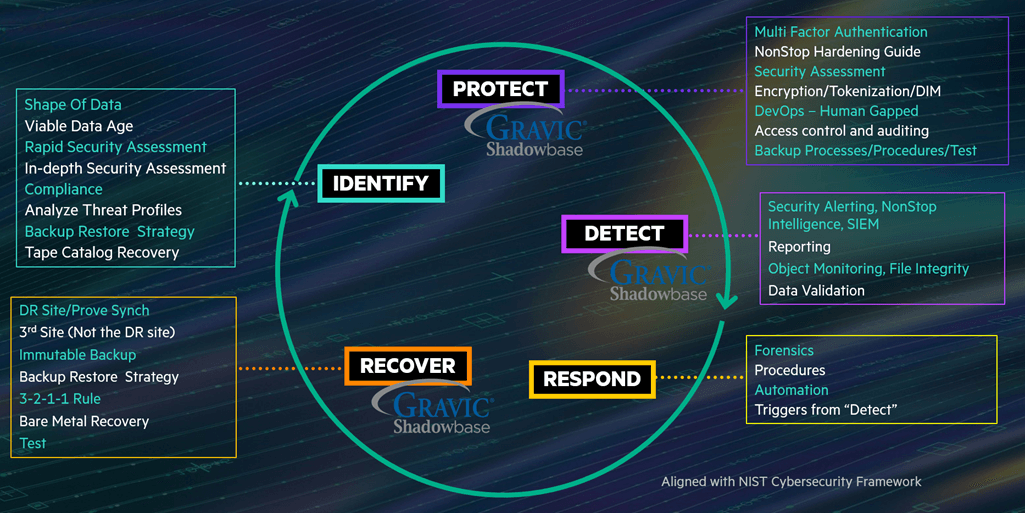
HPE Digital Resiliency Framework based on the NIST* Cybersecurity Standards
As Graham Rogers (HPE) presented during VNUG23, the Framework is a “continuous loop,” meaning it requires constant and continuous efforts to strengthen an enterprise’s Digital Resilience Framework.
Today, state-of-the-art is post-attack Detection and Recovery. Note that this is different than the ultimate goal, pre-attack Identification and Prevention. As solutions develop, Identification and Prevention measures will surface and enable enterprises to shift from being reactive to proactive with their Digital Resilience solutions.
Read the White Paper — Only the Truth: Debunking TMF NonStop Data Protection Myths
Ransomware Recovery System (RRS)*
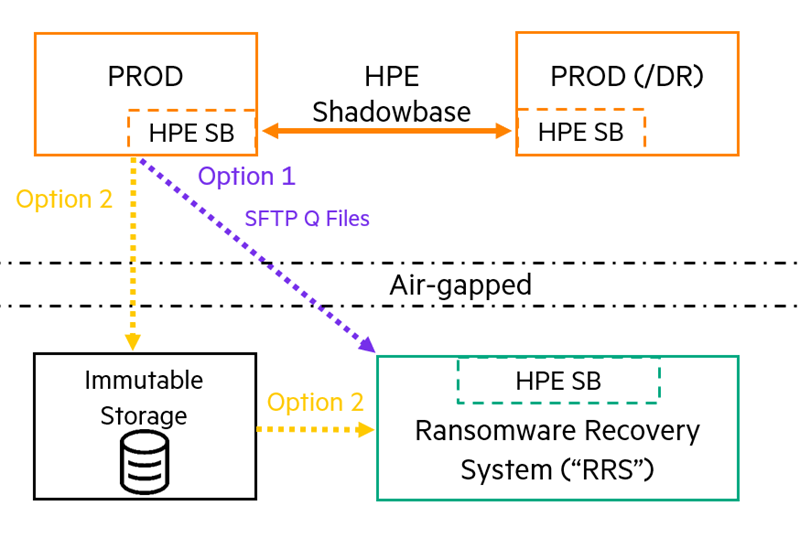
Real-time, Online Recovery System
This architecture satisfies the 3-2-1-1 rule (when leveraging both options); it also provides flexibility:
Architecture 2: Bare Metal Recovery System (BMRS)
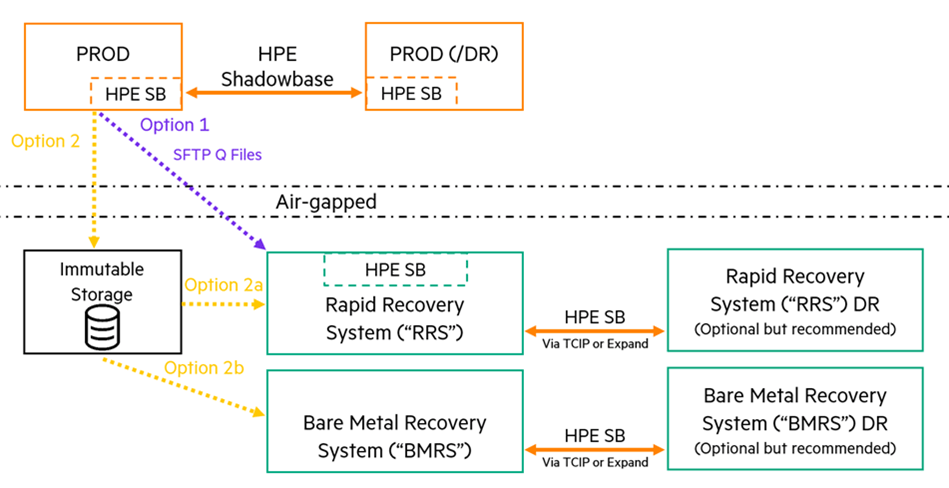
Bare Metal Recovery System (BMRS)
This architecture satisfies the 3-2-1-1 rule, especially with Option 2: Immutable Storage to Air-gapped BMRS. Similar to the previous architecture:
As described above in the HPE Digital Resilience Framework, combatting Malware and Ransomware requires a comprehensive, integrated approach that also involves other solutions (for example, to address Malware that stealthily reads and steals data).
HPE Shadowbase is a critical piece of the HPE Digital Resilience Framework, helping provide an integrated solution and Data Resilience for mission critical NonStop and Other Server environments.
Contact Us to Discuss Your Needs